Introduction
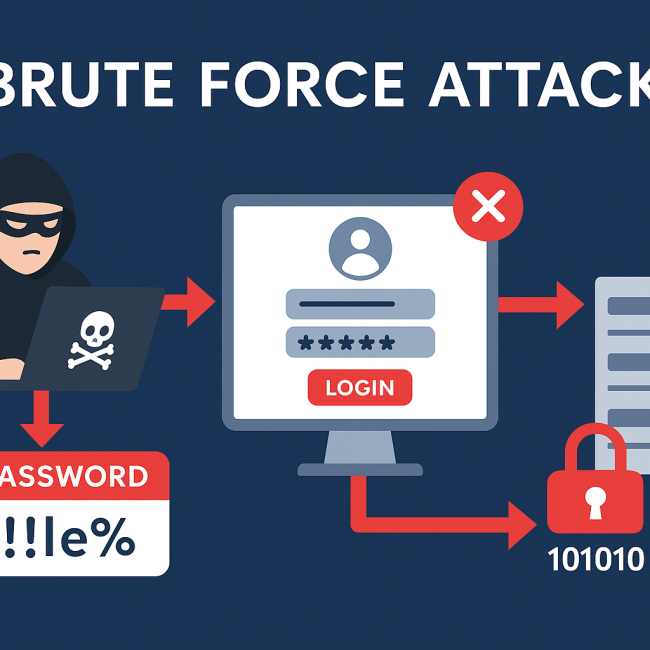
In the age of digitization, the telecom and Internet Service Provider (ISP) industries play a critical role in connecting people, businesses, and governments across the globe. However, this connectivity comes at a cost — the constant threat of cyberattacks. Among the most persistent and disruptive types of attacks is the brute force attack, which targets the fundamental weakness in user authentication systems by attempting to crack credentials through automated guessing.
Brute force attacks impact individual users and pose significant challenges for ISPs and telecom operators who are often the first line of defence against these malicious attempts. This article explores the mechanics of brute force attacks, their implications for telecom infrastructure, and the challenges ISPs face in mitigating these threats.
Understanding Brute Force Attacks
What is a Brute Force Attack?
A brute force attack is a method used by cybercriminals to gain unauthorized access to accounts, systems, or networks by systematically trying all possible combinations of passwords or encryption keys until the correct one is found.
Types of Brute Force Attacks
- Simple Brute Force: Tries all possible combinations.
- Dictionary Attacks: Uses a precompiled list of common passwords.
- Hybrid Attacks: Combines dictionary words with random characters.
- Credential Stuffing: Uses leaked usernames/passwords from other data breaches.
- Reverse Brute Force: A common password is used against many usernames.
Why Brute Force is Still Effective
Despite advancements in cybersecurity, brute force remains a viable attack method due to:
- Weak passwords
- Poor credential management
- Lack of MFA (Multi-Factor Authentication)
- Vulnerable routers, modems, and IoT devices provided by ISPs
How Brute Force Attacks Target ISPs and Telecom Networks
ISPs and telecoms act as gateways to the internet. This central role makes them a prime target for brute force attacks that aim to:
- Compromise routers and modems
- Hijack customer accounts
- Gain access to ISP infrastructure (e.g., Radius servers, billing portals)
- Target DNS, mail servers, and remote access systems (VPN, SSH)
Attackers often scan entire IP ranges assigned to telecoms, searching for open ports and vulnerable systems that allow for brute-force login attempts.
Key Challenges for ISPs and Telecom Operators
- Massive Attack Surface
ISPs manage millions of devices—from home routers and customer-premise equipment (CPEs) to backend servers and IoT gateways. These devices are often:
- Poorly configured
- Using default credentials
- Rarely updated
This wide attack surface makes it extremely difficult to monitor and protect each endpoint.
- Lack of Visibility and Monitoring
Traditional security solutions like antivirus or firewalls aren’t enough. Many ISPs:
- Do not have real-time visibility into login attempts across their networks.
- Cannot differentiate between legitimate users and bots without deep packet inspection (DPI) or behavioral analysis.
- Credential Stuffing at Scale
Because many users reuse passwords across services, credential stuffing becomes a massive issue. ISPs are particularly vulnerable when:
- Their webmail or self-care portals use only basic authentication.
- Customers’ credentials are leaked from third-party breaches.
- Abuse of DNS and Mail Servers
Brute force attacks often use telecom-provided DNS resolvers or mail relays to spread malware, spam, or phishing campaigns. Once compromised, these servers:
- Get blacklisted
- Reduce the quality of service
- Tarnish ISP reputation
- Bandwidth Consumption and Network Load
Continuous brute force attempts:
- Consume excessive bandwidth
- Increase CPU and memory usage on edge devices
- Causes congestion on access networks
- Impact the experience of legitimate users
- Customer Complaints and Churn
When customers are:
- Locked out of accounts,
- Experience slow speeds, or
- Get blacklisted IPs from abuse reports,
They often blame the ISP, not understanding that the root cause lies in a brute-force cyberattack. This increases support costs and affects customer satisfaction and retention.
- Regulatory and Compliance Pressures
In many countries, ISPs are legally required to maintain:
- Log records of access
- Evidence of attacks
- Compliance with cybersecurity frameworks (e.g., NCIIPC, CERT-In, GDPR)
Failure to detect and respond to brute force threats can lead to penalties, legal action, or revocation of licenses.
Advanced Techniques Used by Attackers
Brute force attacks against ISPs are no longer limited to simple login attempts. Modern attackers use:
Botnets
Massive, distributed brute-force attempts using compromised devices (IoT, routers).
IP Rotation
Constantly changing IP addresses to avoid detection and rate-limiting.
Encrypted Traffic
HTTPS-based brute force attacks evade simple firewalls and traditional IDS.
Time-Based and Slow Brute Forcing
Attacks spaced over time to evade detection thresholds.
Mitigation Strategies for ISPs and Telecom Operators
- Rate Limiting and Account Lockouts
Rate limiting login attempts per IP address or per user can significantly reduce brute force success. However, this needs to be tuned carefully to avoid affecting legitimate users.
- CAPTCHA and MFA Integration
Requiring CAPTCHA or two-factor authentication (2FA) for user portals and sensitive systems is an effective deterrent. Many telecom portals still lack MFA support.
- Behavioural Analysis and AI
Using AI-based anomaly detection systems can help ISPs:
- Detect unusual login patterns
- Flag mass login failures
- Identify bot traffic
Platforms like DPI + Network Analysers with machine learning can detect brute-force behaviour at the protocol level.
- Use of Protective DNS
Protective DNS services help block access to known malicious IPs/domains used in brute-force infrastructure. It also prevents redirection to phishing or command-and-control servers.
- Secure Configuration of CPEs
ISPs should:
- Avoid using default usernames/passwords in CPEs.
- Push firmware updates remotely.
- Offer managed routers with enhanced login security.
- Implementing Threat Intelligence Feeds
Incorporating updated blacklists and threat intelligence feeds helps ISPs proactively block traffic from known brute-force botnets and C&C IPs.
- Isolation and Micro-Segmentation
Critical ISP infrastructure (like Radius servers, DNS, and billing platforms) should be isolated through VLANs or segmentation, reducing the blast radius of any compromise.
Real-World Examples of ISP Challenges
- Large-Scale IoT Brute Force (Mirai Botnet)
Mirai used brute-force attacks to access thousands of routers and IoT devices, many of which were on ISP networks using default credentials. It brought down DNS provider Dyn, impacting services like Twitter, Netflix, and Reddit.
- IP Blacklisting and Loss of Email Services
Several ISPs have faced blacklisting from Microsoft, Gmail, and Spamhaus due to brute force botnets abusing their mail relays — resulting in thousands of customers being unable to send email.
- ISP Compromise via SSH Brute Force
Attackers target telecom backend servers using SSH brute force attempts from distributed sources. Once breached, they install ransomware or crypto miners, affecting service availability.
Future Outlook and Recommendations
As brute force attacks evolve, ISPs and telecom operators must shift from reactive to proactive cybersecurity strategies. Key recommendations include:
✅ Zero Trust Architecture
Never trust, always verify — even within internal networks.
✅ Cloud-Based Security Services
Utilize cloud-based firewalls, AI-based login protection, and cloud DNS filtering services.
✅ User Education
Educate customers about strong passwords, changing default credentials, and recognizing phishing attempts.
✅ Security as a Service (SaaS)
Offer premium security packages to customers (e.g., protective DNS, parental control, router hardening) — turning security into a revenue stream.
✅ Regular VAPT and Security Audits
Conduct periodic security assessments and simulate brute force scenarios to test response effectiveness.
Brute force attacks are not just a nuisance — they represent a growing cybersecurity challenge that ISPs and telecom operators must address head-on. The vast scale of networks, connected devices, and human factors involved makes the problem complex, but not insurmountable.
With a combination of smart security practices, modern technologies like AI and DNS protection, and an educated customer base, ISPs can not only protect their networks but also differentiate themselves as secure service providers in an increasingly hostile digital environment.
Xelelabs offers a cutting-edge solution specifically designed to protect ISP and telecom infrastructure from brute force attacks. Our technology integrates protective DNS, behavioural threat detection, and advanced IP filtering to detect and block brute force attempts in real-time, without the need for any software installation at the customer end. Whether you’re an ISP, telecom operator, or enterprise network provider, Xelelabs empowers you to deliver secure, uninterrupted services to your users with confidence.